How to verify if the wireless network is vulnerable to Key Reinstallation Attack (KRACK)?
Key Reinstallation Attack (KRACK) is a critical flaw in the WPA2 protocol (CVE-2017-13077 to CVE-2017-13088):
1. Understand KRACK Vulnerability
KRACK exploits the WPA2 4-way handshake to force the reinstallation of an already-used encryption key, allowing attackers to:
- Decrypt network traffic.
- Inject malicious packets (e.g., ransomware, malware).
- Hijack client connections.
Affected Devices:
- All WPA2 networks (Personal and Enterprise).
- Clients (laptops, smartphones, IoT) and access points (APs) with outdated firmware.
2. Tools Required
- A wireless NIC supporting monitor mode (e.g., Alfa AWUS036ACH).
- Linux machine (Kali Linux recommended).
- Scripts/Tools:
krack-test(GitHub)airodump-ng(capture handshakes).Wireshark(analyze packets).scapy(craft custom packets).
3. Testing Steps
A. For WPA2-Personal (PSK) Networks
Capture the 4-Way Handshake:
- Start monitoring the target network:
airodump-ng -c <channel> --bssid <AP_MAC> -w capture wlan0mon - Wait for a client to connect (or deauth a client to force reconnection):
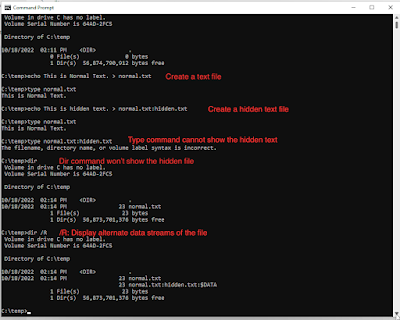
aireplay-ng -0 1 -a <AP_MAC> -c <Client_MAC> wlan0mon - Verify the handshake is captured using
aircrack-ng capture.cap.
- Start monitoring the target network:
Test for KRACK Using
krack-test:- Clone the KRACK test suite:
git clone https://github.com/vanhoefm/krackattacks - Run the test script against the captured handshake:
./krack-test.py --pcap capture.cap - Vulnerability Indicators:
- Script detects retransmitted Message 3 or Group Key Handshake.
- Wireshark shows replayed/duplicate handshake messages.
- Clone the KRACK test suite:
B. For WPA2-Enterprise (802.1X) Networks
- Capture the 4-Way Handshake (same as above).
Exploit the Extended Key ID (if supported):
- Enterprise networks use key separation, but some implementations reuse keys.
- Use
scapyto forge retransmissions of handshake messages:# Example: Replay Message 3 of the 4-way handshake sendp(radio_tap/ieee80211/dot11_4whs_msg3, iface="wlan0mon", count=10) - Monitor if the client re-installs the PTK (Pairwise Transient Key).
Check for Client/AP Patches:
- Most modern devices (post-2017) are patched.
- Manually verify firmware versions of APs/clients (e.g., Cisco, Aruba, Windows 10+).
4. Signs of Vulnerability
Active Exploitation:
- Attackers can decrypt traffic using tools like
ettercaporwireshark. - Clients disconnect or experience instability during testing.
- Attackers can decrypt traffic using tools like
Passive Detection:
- APs/clients accept retransmitted handshake messages.
- No encryption errors when replaying packets.
5. Remediation
Patch All Devices:
- Update AP firmware (e.g., Cisco, Ubiquiti, OpenWRT).
- Ensure client OSes are updated (Windows, iOS, Android, Linux).
Enable WPA3:
- WPA3 uses Simultaneous Authentication of Equals (SAE) and is immune to KRACK.
Disable Legacy Protocols:
- Remove support for WPA-TKIP and WEP.
6. Automated Scanners
- Nessus/Qualys: Use vulnerability scanners to detect unpatched APs/clients.
- Acrylic Wi-Fi Professional: Scans for KRACK vulnerabilities in networks.
Example of a Vulnerable Network
# Running krack-test.py
[+] Detected retransmitted Message 3 in 4-way handshake.
[!] AP is vulnerable to CVE-2017-13077 (Key Reinstallation).
Note: KRACK primarily exploits client-side vulnerabilities, so even if the AP is patched, unpatched clients remain at risk. Always test both ends of the connection!